Background
OAuth in Dify involves two separate flows that developers should understand and design for.Flow 1: OAuth Client Setup (Admin / Developer Flow)
On Dify Cloud, Dify team would create OAuth apps for popular tool plugins and set up OAuth clients, saving users the trouble to configure this themselves.Admins of Self-Hosted Dify instances must go through this setup flow.
Create a Google Cloud Project
Create a Google Cloud Project
- Go to Google Cloud Console and create a new project, or select existing one
- Enable the required APIs (e.g., Gmail API)
Configure OAuth Consent Screen:
Configure OAuth Consent Screen:
- Navigate to APIs & Services > OAuth consent screen
- Choose External user type for public plugins
- Fill in application name, user support email, and developer contact
- Add authorized domains if needed
- For testing: Add test users in the Test users section
Create OAuth 2.0 Credentials
Create OAuth 2.0 Credentials
- Go to APIs & Services > Credentials
- Click Create Credentials > OAuth 2.0 Client IDs
- Choose Web application type
- A
client_idand aclient_secretwill be generated. Save these as the credentials.
Enter Credentials in Dify
Enter Credentials in Dify
Enter the client_id and client_secret on the OAuth Client configuration popup to set up the tool provider as a client.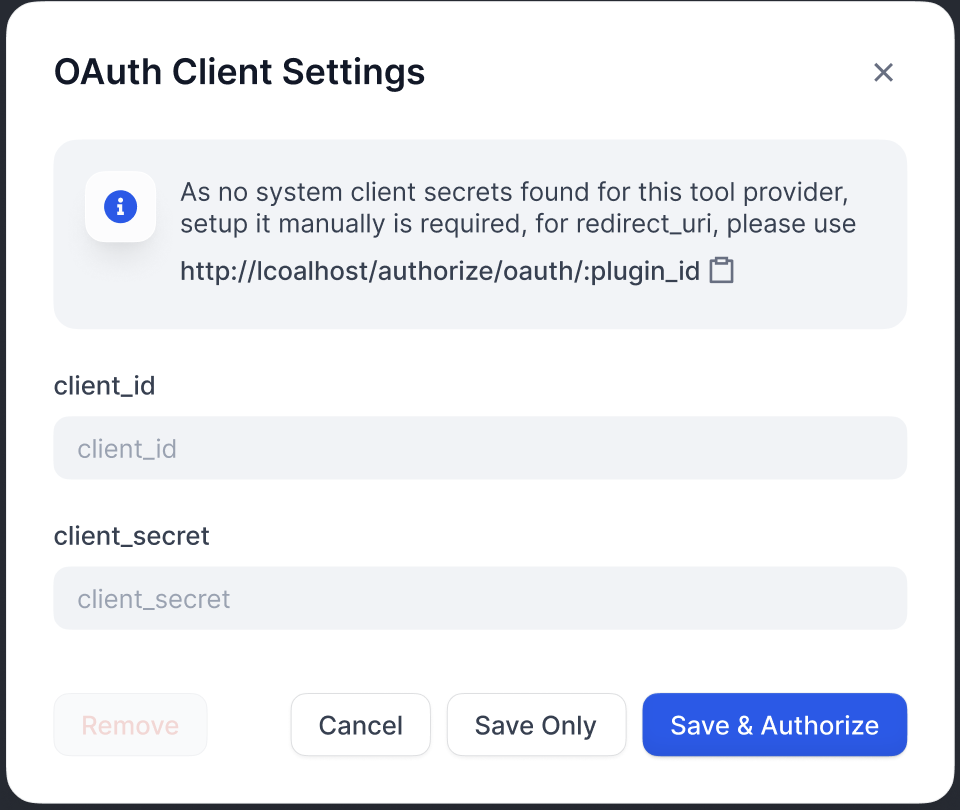

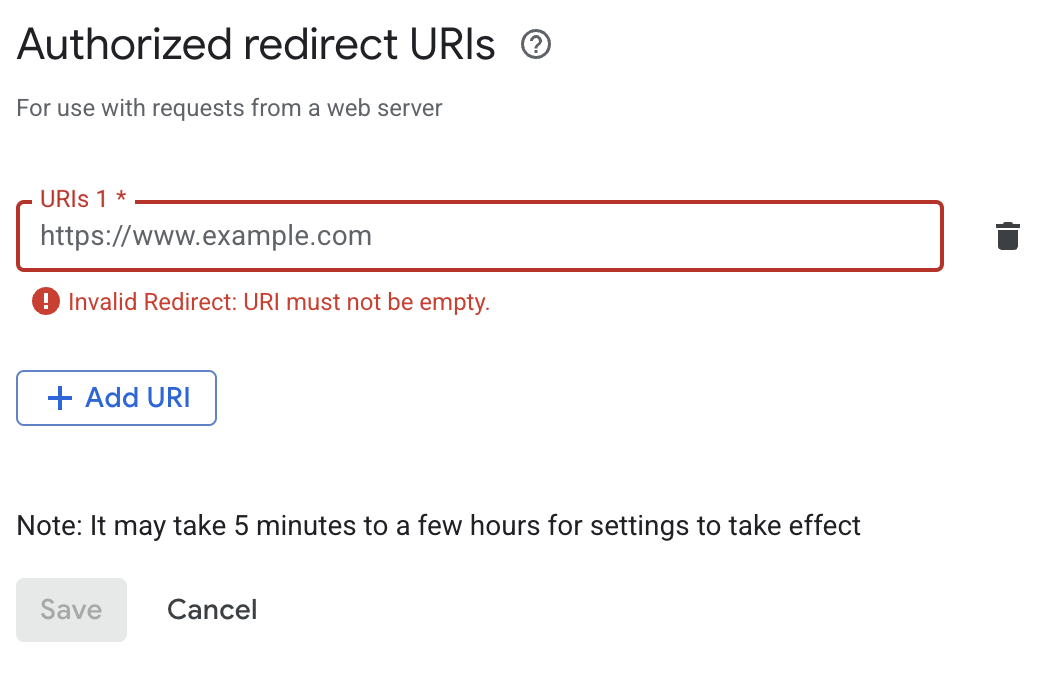
Authorize Redirect URI
Authorize Redirect URI
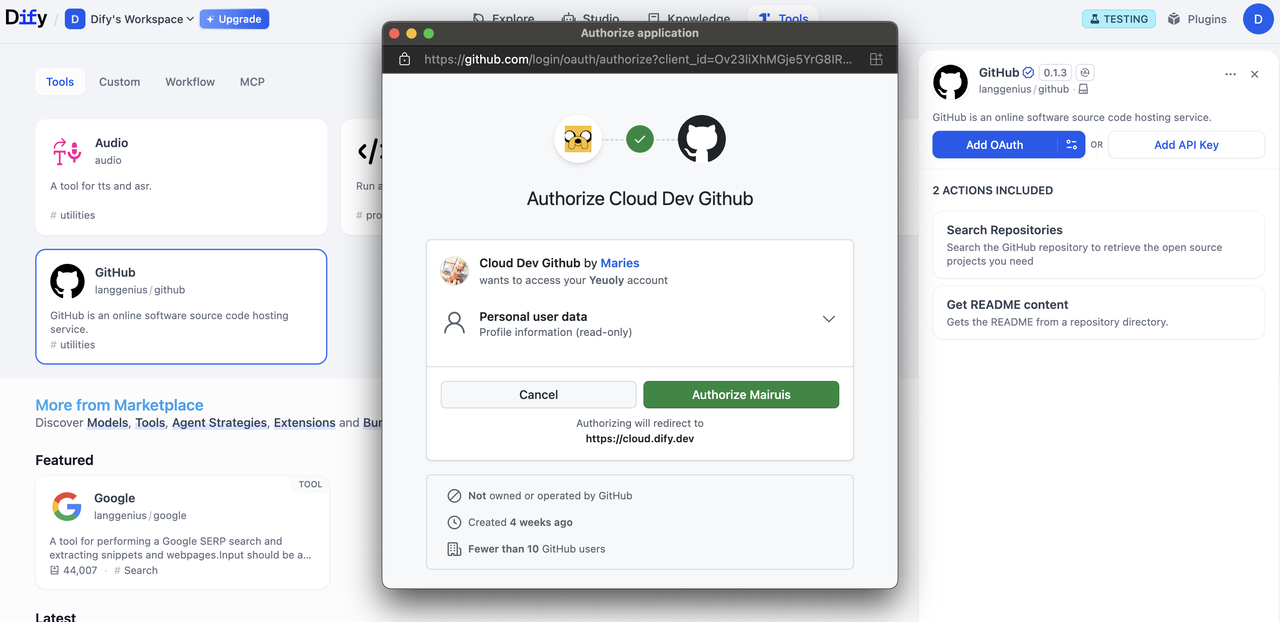
Flow 2: User Authorization (Dify User Flow)
After configuring OAuth clients, individual Dify users can now authorize your plugin to access their personal accounts.
Implementation
1. Define OAuth Schema in Provider Manifest
Theoauth_schema section of the provider manifest definitions tells Dify what credentials your plugin OAuth needs and what the OAuth flow will produce. Two schemas are required for setting up OAuth:
client_schema
Defines the input for OAuth client setup:gmail.yaml
The
url field links directly to help documentations for the third-party service. This helps confused admins / developers.credentials_schema
Specifies what the user authorization flow produces (Dify manages these automatically):Include both
oauth_schema and credentials_for_provider to offer OAuth + API key auth options.2. Complete Required OAuth Methods in Tool Provider
Add these imports to where yourToolProvider is implemented:
ToolProvider class must implement these three OAuth methods (taking GmailProvider as an example):
3. Access Tokens in Your Tools
You may use OAuth credentials to make authenticated API calls in yourTool implementation like so:
self.runtime.credentials automatically provides the current user’s tokens. Dify handles refresh automatically.
For plugins that support both OAuth and API_KEY authentication, you can use self.runtime.credential_type to differentiate between the two authentication types.
4. Specify the Correct Versions
Previous versions of the plugin SDK and Dify do not support OAuth authentication. Therefore, you need to set the plugin SDK version to:manifest.yaml, add the minimum Dify version:
Edit this page | Report an issue